Generate Tls Certificate And Key
Creating a TLS encryption key and certificate (If you are unfamiliar with the abbreviation “ TLS “: it is the successor to SSL.) The internet is the best invention since sliced bread but it has become an evil place more than ever. Mar 29, 2020 How To Create A Free TLS Certificate. Here we take a look at the step by step procedure to create a free TLS certificate. Get a domain, DNS, and hosting. Before even thinking of getting a TLS certificate, you must have a domain you want to use it for.
- Generate Tls Certificate Linux
- Generate Tls Certificate And Key Code
- Generate Server Certificate Openssl
- If you don't have a private key and a corresponding SSL/TLS certificate to use for HTTPS, you can generate a private key on an HSM. You can then you use the private key to create a certificate signing request (CSR).
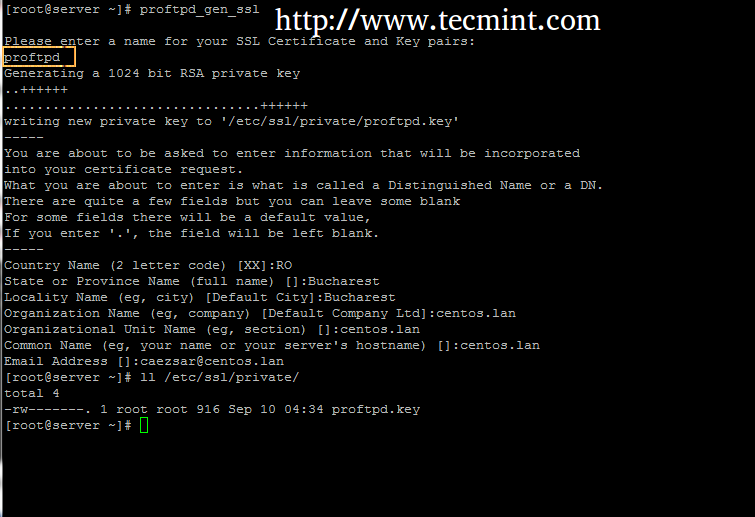
- Create the SSL Certificate. Now that we know the basics, let’s see how we can create a self-signed TLS/SSL certificate and configure it within our Apache and/or Nginx servers. The first thing to do is to create a / etc / ssl / private / folder on the server, which we’ll use to store the SSL/TLS key files. Since the secrecy of this key is.
Updated by LinodeWritten by Linode
Report an Issue View File Edit File
What is a Self-Signed TLS Certificate?
Self-signed TLS certificates are suitable for personal use or for applications that are used internally within an organization. If you intend to use your SSL certificate on a website, see our guide on enabling TLS for NGINX once you’ve completed the process outlined in this guide.
Create the Certificate
Change to the
rootuser and change to the directory in which you want to create the certificate and key pair. That location will vary depending on your needs. Here we’ll use/root/certs:Create the certificate:
You will be prompted to add identifying information about your website or organization to the certificate. Since a self-signed certificate won’t be used publicly, this information isn’t necessary. If this certificate will be passed on to a certificate authority for signing, the information needs to be as accurate as possible.
The following is a breakdown of the OpenSSL options used in this command. There are many other options available, but these will create a basic certificate which will be good for a year. For more information, see
man opensslin your terminal.-newkey rsa:4096: Create a 4096 bit RSA key for use with the certificate.RSA 2048is the default on more recent versions of OpenSSL but to be sure of the key size, you should specify it during creation.-x509: Create a self-signed certificate.-sha256: Generate the certificate request using 265-bit SHA (Secure Hash Algorithm).-days: Determines the length of time in days that the certificate is being issued for. For a self-signed certificate, this value can be increased as necessary.-nodes: Create a certificate that does not require a passphrase. If this option is excluded, you will be required to enter the passphrase in the console each time the application using it is restarted.
Here is an example of the output:
Restrict the key’s permissions so that only
rootcan access it:Back up your certificate and key to external storage. This is an important step. Do not skip it!
Join our Community
This guide is published under a CC BY-ND 4.0 license.
SSL/TLS certificate has turned out a worth considering solution for web security. Still many people know little about SSL and its core practices. It is true that in modern cybercrime age if you ignore web security, it could put your business in the drastic situation resulting in loss of money and business reputation. Some websites have been ignoring the use of SSL/TLS, as it is not in the interest of customers. This article is designed to encourage website owners in implementing SSL on their website and make aware of few terms that are used in SSL.
What SSL/TLS offers?
SSL certificates has its inherent features that make SSL stand out in the industry. Encryption not only is a goal of SSL certificate but also provides authentication of business identity, data privacy and easy exchange of information. Every SSL/TLS certificate as per new NIST and CA/browser guideline are having a modern and robust algorithm to make the online environment safe.
- Authentication: In SSL, a user visits a website meanwhile the server sends a copy of a certificate to the user’s browser to make it known that the browser is connecting to the right website. The data of a server certificate includes domain name and company’s information. Moreover, the browser upon visiting SSL secured site shows a green padlock to ensure visitors that the website is safe for online deals.
- Data integrity: SSL ensures data integrity, It means the data is not altered during the transition. Because of strong encryption, the network attacker cannot damage or change the content between the user and the web server. The message/data is confirmed through Message authentication code.
- Data confidentiality: Data confidentiality prevents data from being exposed to third party or attackers. It would become hard to intercept the encrypted data for attackers thus the data remains confidential between two endpoints.
SSL and TLS Protocols Explained
In the world of cryptography, there are mainly SSL (Secure Socket Layer) and TLS (Transport Layer Security) protocols. Both protocols are widely used in most email, application, VoIP.
SSL
SSL has mainly three protocol versions SSL 1.0, SSL 2.0 and SSL 3.0 and all are deprecated. Currently, TLS 1.2 is in force.
However, Netscape has developed SSL protocols. Initially, SSL 1.0 was developed but was never released in public due to security flaws.
After the development of SSL 1.0, Netscape came with SSL 2.0 in February 1995 but did not do well with same reason of security flaws.
Generate Tls Certificate Linux
SSL 2.0 was susceptible to Drown attack and could be used to attack RSA keys with the same name even if the same public key certificate is used on different servers. SSL 2.0 server leaks public key details that can be used against TLS server.
SSL 3.0 was released in 1996 and supports certificate authentication as well added SHA-1 based ciphers. However, SSL 3.0 carries weak key derivation process where the master key depends upon MD5 hash function (irresistible to collision attack). In October 2014, SSL 3.0 was deemed weak against padding attack. The chain of certificate is established in SSL3.0 that allowed organizations to use certificate hierarchy.
TLS
If we look at the history of TLS, there was main three version of TLS has been released until the date.
TLS 1.0 was defined RFC2246 in January 1999. TLS 1.0 worked on symmetric encryption (DES, RC4). Each encryption is generated unique for individual connection and is based on shared secret, which is negotiated at the beginning of a session.
TLS 1.1 was specified in RFC4346 in the month of April of 2006. It was an upgrade to TLS 1.0 version and was ideal protection against CBC (cipher-block chaining) attacks. TLS 1.1 supports IANA registration parameters.
TLS 1.2 was specified in RFC5246 in August 2008 that comes with modern authenticated encryption. At present, TLS 1.2 version is accepted and believed to be free from any attack.
How to Get SSL/TLS Certificate?
SSL order process follows simple steps as below.
- First, you have to select desired SSL product.
Validated
Certificates
Server (UCC)
- Create CSR (certificate signing request) from your server and paste it into Notepad.
- Now, you have to buy your SSL/TLS certificate product as per your business needs.
- Once you pay for selected certificate, you will receive unique configuration link.
- Submit generated CSR to start the authentication procedure and wait for order request.
- The certificate authority will send your SSL Certificate via email.
- Now, install the certificate on your desired server and don’t forget to implement “Secure Site Seal” on your website.
Glossary:
CSR (Certificate Signing Request):
CSR is called Certificate Signing Request. A CSR includes data like organization’s name, domain name, location, town, city, email address and is submitted at the time of ordering a certificate. The CA considers CSR information to confirm and create your SSL certificate. Most importantly, it also holds the public key that will be contained in your certificate.
Different Types of SSL/TLS Validations:
SSL/TLS certificate price depends upon the type of validation that certificate authority will follow to issue your certificate.

- Domain Validation: The certificate authority verifies the ownership of a domain and ensures that the domain name belongs to the SSL applicant. Such certificate can be issued within 15 minutes.
- Organization Validation: Organization validation establishes the identity of a business and requires business related documents to verify business existence.
- Extended Validation: Extended Validation follows a strict and lengthy process and includes domain and business verification. The process checks the legal, operational and physical existence of the entity by following EV guidelines that define vetting policies and principles.
Site Seal:
Site seal comes at free of cost when you purchase SSL certificate. Site seal is a logo that ensures visitors and customers that the website is secured. The site seal assures that any online transactions will be done in a secure environment.
Public Key Cryptography:
Keys play a vital role in SSL certificate that are based on asymmetric encryption. These keys named private key and public key.The data encrypted with public key can only be decrypted with private key. A strong keys means there are fewer chances of spying and interception.
Public Key and Private Key:
Public key is a part of public-key cryptography/asymmetric cryptography that uses pair of keys: public key and private key. Public key is disseminated among users. The messages are encrypted with public key can only be decrypted with private key. The use of two keys named asymmetric cryptography and the system that use public key is named as PKI (public key infrastructure).
Private Key is used to decrypt the message. Whatever encrypted with public key can only be decrypted with its private key pair. A strong private key prevents information from spying and data sniffing. It is advisable to generate private key on trusted computer with proper security. At present, many certificate authorities use 2048-bit RSA key.
Reliable Certificate Authority:
Securing online identity can be achieved with authenticated SSL certificate that should be backed by legitimate certificate authority (CA). There are self-signed certificates that do not carry reliability hence, browsers show warning while coming across with it. Legitimate CA ensures that the traveling information between the browser and the server will be encrypted with robust encryption and the third party would not be able to intercept it. At present, below leading certificate authorities are proved their existence in SSL industry.
Certificates
Certificates
Certificates
Root SSL Certificate:
There are two certificates: root certificate and intermediate certificate. To make the certificate trusted by device and browser, the role of a root certificate comes into play. The root certificate is created by the certificate authority and is recognized by software applications, browsers. The purpose of the root certificate is to create a chain of trust and the browser will trust all certificates inherently trust all certificates that are signed by root certificate. When a user visits the website, the browser starts the verification of certificate by following chain of trust linked with root certificate.
ECC Algorithm:
As the size of RSA keys increases, it can cause performance issue. To solve this issue, ECC (Elliptic Curve Cryptography) is introduced, which follows smaller and faster key generation along with the same level of encryption strength. ECC can produce a 164-bit key level of security compare to 1024-bit RSA key.
Always-On SSL:
Generate Tls Certificate And Key Code
It is a misconception that SSL is used only for login or checkout page, but it is false. When you secure a particular page, the rest pages of a website remain unencrypted and hackers can take advantage of those pages. Therefore, Always-On SSL can secure the whole website including image, Java script, cookies and session and save the site from Sidejacking and SSL Strip attack.
Generate Server Certificate Openssl
SSL is a protocol that creates a secure tunnel to travel information in a secured environment. The above information is related to quick guide on SSL best practices that will help once you go with SSL certificate or want to know about SSL practices to be followed in SSL industry.
