Dh Public Key Generation C Code
2.4 The ElGamal public key cryptosystem Although the Di–eHellman key exchange algorithm provides a method of publicly sharing a random secret key, it does not achieve the full goal of being a public key cryptosystem, since a cryptosystem permits exchange of speciflc information, not just a random string of bits. The flrst public key cryptosys. KeyPairGenerator is an engine class which is capable of generating a private key and its related public key utilizing the algorithm it was initialized with. Nov 04, 2014 Get YouTube without the ads. 1 month free. Find out why Close. The RSA Encryption Algorithm (2 of 2: Generating the Keys). Understanding ECC through the Diffie-Hellman. I want to write a complete diffie Hellman example for bouncy castle that includes key generation, key exchange, encryption, and decryption. I also want to verify that if Alice is initiating a connection to Bob, that she should send her public key, Parameter P, and Parameter G. DHgeneratekey performs the first step of a Diffie-Hellman key exchange by generating private and public DH values. By calling DHcomputekey, these are combined with the other party's public value to compute the shared key. DHgeneratekey expects dh to. Our doors are always open. Mbed TLS is fully open-source. There are no hidden features, privileged applications or non-public management tools. Everything we have, we make open source and is accessible from our site.
- Key Generation Software
- Dh Public Key Generation C Code Lookup
- Dh Public Key Generation C Code Free
- Dh Public Key Generation C Codes
- Dh Public Key Generation C Code Download
Key Generation Software
Tiny ECDH / ECC in C
This is a small and portable implementation of the Elliptic-Curve Diffie-Hellman key agreement algorithm written in C.
Description from Wikipedia:
Elliptic-curve Diffie–Hellman (ECDH) is an anonymous key agreement protocol that allows two parties, each having an elliptic-curve public–private key pair, to establish a shared secret over an insecure channel. This shared secret may be directly used as a key, or to derive another key. The key, or the derived key, can then be used to encrypt subsequent communications using a symmetric-key cipher. It is a variant of the Diffie–Hellman protocol using elliptic-curve cryptography.`
Dh Public Key Generation C Code Lookup
You can choose between 10 standard NIST curves of different sizes. 5 pseudo-random curves and 5 Koblitz curves providing from 80 to 256 bits symmetrically equivalent security. See ecdh.h for clarification.
You can define the macro ECDH_COFACTOR_VARIANT in ecdh.c to enable the co-factor variant of ECDH for safe non-ephemeral use.
The API is very simple and looks like this (I am using C99 <stdint.h>-style annotated types):
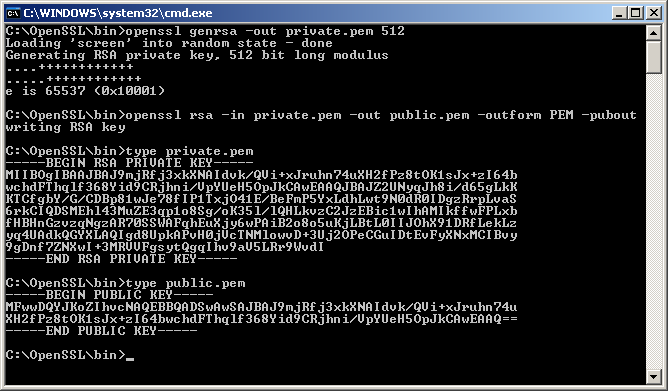
You need to provide random data for the private key yourself, for the key generation process.See ecdh_example.c for an example of how to use the library.
There is no built-in protection from out-of-bounds memory access errors as a result of malicious input. The two functions ecdh_shared_secret() and ecdh_generate_keys() expect inputs of a certain length. See ecdh.h for clarification.
The module allocates no RAM internally and takes up 2.1K ROM when compiled for ARM (1.4K for Thumb but YMMV).A keypair requires between 72 and 216 bytes of RAM depending on which curve you choose (i.e. how big the underlying base field is).
It is the smallest implementation of ECC in C I've seen yet, but do contact me if you know of something smaller (or have improvements to the code here).
Dh Public Key Generation C Code Free
I am using the Free Software Foundation, ARM GCC compiler:
All material in this repository is in the public domain.
Dh Public Key Generation C Codes
TODO:
Dh Public Key Generation C Code Download
- Implement ECDSA signing and verifification.