Bash Ssh Generate Key Login Without Password
The SSH protocol recommended a method for remote login and remote file transfer which provides confidentiality and security for data exchanged between two server systems. The SSH depends upon the use of public key cryptography. The OpenSSH server offers this kind of setup under Linux or Unix-like system. This how-to covers generating and using ssh public keys for automated usage such as:
- Bash Ssh Generate Key Login Without Password Linux
- Ssh Generate Key Unix
- Setup Ssh Without Password
- Bash Ssh Generate Key Login Without Password Windows 7
- Linux Ssh Without Password
I tried with both options, first I rename idrsa and second rename and change location of idrsa and also delete permanently idrsa from /.ssh/ location, but same result. Ssh allow access without key and password. I want security in every ssh login attempt. – Tejas Virpariya Mar 28 '18 at 18:29.
- SSH (Secure Shell) is a cryptographic network protocol which is used for establishing secure connections between a remote client and a server, using the TCP protocol for security and reliability. SSH based connections support various authentication methods, some of them being: Password based authentication; Key based authentication.
- Oct 20, 2014 If you were able to login to your account using SSH without a password, you have successfully configured SSH key-based authentication to your account. However, your password-based authentication mechanism is still active, meaning that your server is still exposed to brute-force attacks.
- Automated Login using the shell scripts
- Making backups
- Run commands from the shell prompt and more
- Login without password
How to configure SSH Public key-based authentication for a Linux/Unix
The steps and commands are as follows:
- On your local system type: ssh-keygen
- Install public key into remote server: ssh-copy-id user@remote-server-ip-name
- Use ssh for password less login: ssh user@remote-server-ip-name
Let us see all commands in details.
Generating SSH Keys
First, log on to your workstation. For example, log on to workstation called admin.fbsd.nixcraft.org as vivek user. Please refer the following sample setup. You will be logged in, on your local system, AS THE USER you wish to make passwordless ssh connections.
To create the cryptographic keys on your local system powered by FreeBSD/Linux/macOS/ UNIX workstation, enter:ssh-keygen -t rsa
Assign the pass phrase (press [enter] key twice if you don’t want a passphrase). It will create 2 files in ~/.ssh directory as follows:
- ~/.ssh/id_rsa : identification (private) key
- ~/.ssh/id_rsa.pub : public key
How to copy a public ley (~/.ssh/id_rsa.pub) to your server
Use the scp command to copy the id_rsa.pub (public key) from your local system to rh9linux.nixcraft.org remote server as authorized_keys file, this is know as, “installing the public key to server”:scp ~/.ssh/id_rsa.pub vivek@rh9linux.nixcraft.org:~/.ssh/authorized_keys
Another option is to use the ssh-copy-id command as follows from your local workstation:ssh-copy-id user@remote-box
ssh-copy-id -i ~/.ssh/id_rsa.pub vivek@rh9linux.nixcraft.org
How to login to your remote server using SSH keys
From your local system (e.g. FreeBSD/macOS/Linux/Unix workstation) type the following command:ssh user@remote-box
ssh vivek@rh9linux.nixcraft.org
Changing the pass-phrase on workstation
To change a passphrase for your ssh keys, use the ssh-keygen command as follows:ssh-keygen -p
ORcd ~/.ssh/
ssh-keygen -f id_rsa -p
How to use ssh-agen command
You can use the ssh-agent command to avoid continues passphrase typing at the CLI:ssh-agent $SHELL
ssh-add
Now ssh server will not use prompt for the password. Above two commands can be added to your ~/.bash_profile file so that as soon as you login into workstation you can set the agent.
Deleting the keys hold by ssh-agent
To list keys, enter:ssh-add -l
To delete all keys, enter:ssh-add -D
To remove specific key, enter:ssh-add -d key
See also:
- Man pages: sshd(8),ssh(1),ssh-add(1),ssh-agent(1)
ADVERTISEMENTS
Set up your first SSH keys
Use SSH keys for authentication when you are connecting to your server, or even between your servers. They can greatly simplify and increase the security of your login process. When keys are implemented correctly they provide a secure, fast, and easy way of accessing your cloud server.
Follow our guide and learn how to set up your first SSH keys for authentication using OpenSSH or PuTTYTray.
Preparing your server
To add an SSH key pair, first, create a hidden folder to your user account home directory on your cloud server with the following command.
Then restrict the permissions to that directory to just yourself with the command below.
This creates a secure location for you to save your SSH keys for authentication. However, note that since the keys are stored in your user home directory, every user that wishes to connect using SSH keys for authentication has to repeat these steps on their own profile.
Using OpenSSH to generate a key pair
Now continue on your own computer if you are using Linux or any other OS that has OpenSSH. PuTTY users should skip to the next section.
1. Generate a new key pair in a terminal with the next command
The key generator will ask for location and file name to which the key is saved to. Enter a new name or use the default by pressing enter.
Bash Ssh Generate Key Login Without Password Linux
2. (Optional) Create a passphrase for the key when prompted
This is a simple password that will protect your private key should someone be able to get their hands on it. Enter the password you wish or continue without a password. Press enter twice. Note that some automation tools might not be able to unlock passphrase-protected private keys.
3. Copy the public half of the key pair to your cloud server using the following command
Replace the user and server with your username and the server address you wish to use the key authentication on.
This also assumes you saved the key pair using the default file name and location. If not, just replace the key path ~/.ssh/id_rsa.pub above with your own key name.
Enter your user account password for that SSH server when prompted.
You can now authenticate to your server with the key pair, but at the moment you would need to enter the passphrase every time you connect.
4. (Optional) Set up SSH Agent to store the keys to avoid having to re-enter passphrase at every login
Enter the following commands to start the agent and add the private SSH key.
Type in your key’s current passphrase when asked. If you saved the private key somewhere other than the default location and name, you’ll have to specify it when adding the key.
Afterwards, you can connect to your cloud server using the keys for authentication, and only having to unlock the key by repeating the last 2 steps once after every computer restart.
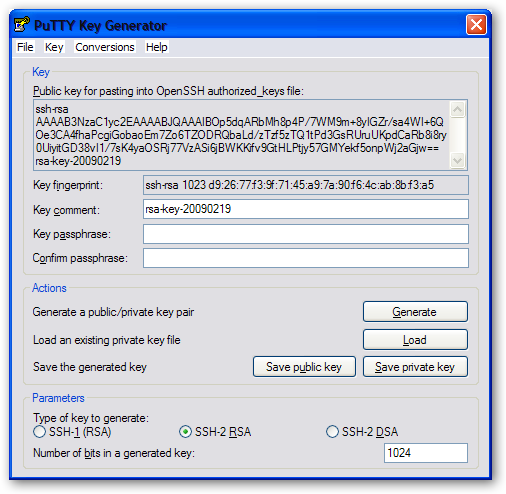
Using PuTTYTray to generate a key pair
If you are running Windows and PuTTYTray for SSH, you can use the built-in key generator from PuTTY to create a new key pair.
1. Click the Keygen button at the bottom of the PuTTY Configuration window to get started.
Then in the Key Generator window, check that the Type of key to generate at the bottom is set to SSH-2 RSA. The older SSH-1 was the first version on the standard but is now generally considered obsolete. Most modern servers and clients support SSH-2.
2. Click the Generate button to begin.
3. Keep moving your mouse over the blank area in any manner to help generate randomness for a few moments until the progress is complete.
With the keys finished, PuTTY will show the relative information about the pair along with the public key for easier copying.
4. (Optional) Enter a key passphrase in the 2 empty fields for the added security before continuing. The passphrase will protect your key from unauthorized use should someone be able to copy it. However, some automation tools might not be able to unlock passphrase-protected private keys.
5. Click the Save private key button and store it somewhere safe. Generally anywhere in your user directory is fine as long as your PC is password protected. Before closing the keygen, you may want to copy the public key to your clipboard, but you can always get it later as well.
Now that you have a new key saved on your computer, you’ll need to import it into the PuTTY key agent.
6. Click the Agent button to open the key manager in the PuTTY Configuration window.
7. Click Add Key button in the Key List, then browse to the location you saved the private key, select it and click Open.
Enter your key passphrase if asked.
This will import the key to your PuTTY client, but you still need to copy the public key over to your server.
8. Open an SSH connection to your cloud server and go to the SSH key directory.
9. Open or create the default file OpenSSH looks for public keys called authorized_keys.
Sniper Elite V2 steam key generator telecharger file is 100% clean and safe, no hidden ads or offers, we use only open source technologies, full code is available for you to edit or upate. Sniper Elite V2 steam key generator telecharger supports wide range of platforms, such as Windows and Mac OS X. Sniper Elite V2 Remastered cd key generator keygen has been published after epic three weeks beta testing, which ended with great success. This tool will NOT let you down. This tool will NOT let you down. You are elite sniper Karl Fairburne, parachuted into Berlin amidst the Germans’ final stand. Your mission is to prevent Nazi V2 rocket technology falling into the hands of the Red Army. You must aid key scientists keen to defect to the US, and terminate those who stand in your way. Sniper elite v2 steam key generator.
10. Paste the public key into the file by simply right-clicking the SSH client window. Make sure the key goes on a single line for OpenSSH to be able to read it.
When you’ve copied the public key over to the authorized keys list, save the file and exit the editor. You can now test the public key authentication by logging in to your server again. You should not get asked for your password, but instead logged straight in with the key. If it’s not working, check that your private key is unlocked at your SSH Agent and try again.
Ssh Generate Key Unix
Turn off password authentication
With SSH key authentication configured and tested, you can disable password authentication for SSH all together to prevent brute-forcing. When logged in to your cloud server.
1. Open the SSH configuration file with the following command.
2. Set the password authentication to no to disable clear text passwords. Adobe photoshop cs 8 key generator.
3. Check that public key authentication is enabled, just to be safe and not get locked out from your server. If you do find yourself unable to log in with SSH, you can always use the Web terminal at your UpCloud control panel.
Setup Ssh Without Password
Then save and exit the editor.
Bash Ssh Generate Key Login Without Password Windows 7
4. Restart the SSH service to apply the changes by using the command below.
Linux Ssh Without Password
With that done your cloud server is now another step along towards security. Malicious attempts to connect to your server will results in authentication rejection, as plain passwords are not allowed, and brute-forcing an RSA key is practically impossible.
Conclusions
Remember to always keep your private keys safe. You can use the same key from multiple computers if you wish, or generate new ones on each client connecting to your cloud server for added security. Each user should generate their own key pair and passphrase for secure access control. With proper management, even in case one of the private keys gets compromised you won’t have to replace them all.